Economical & Best CCNA, MCITP, CCNP, CCIE, Ethical Hacking, LINUX Training in Hyderabad from Industry top Trainers.
Tuesday, December 31, 2013
Thursday, December 5, 2013
Monday, October 21, 2013
Register for Free Online Training Demo
Zoom is offering Online Training on the following technologies :
CCNA (R&S), CCNP, CCIE, MCSE-Windows Server 2012, MS Exchange Server 2013, Linux, Ethical Hacking & Counter Measures, CCNA (Security),VMware
Monday, August 19, 2013
Application for Employment / Job -- By Job Searching Expert
Application for Employment / Job -- By Job Searching Expert

Which is the best data tunneling protocol for a Windows 7 VPN?
There are 4 different types of data tunneling protocols available. These are:
PPTP or Point-to-Point Tunneling Protocol
L2TP IPSec or Layer 2 Tunneling Protocol with Internet Protocol Security
SSTP or Secure Socket Tunneling Protocol
IKEv2 or Internet Key Exchange Version 2
Windows 7 supports compatibility with all of the aforementioned 4 data
tunneling protocols but the best protocol is the one that offers the
safest data tunnel with seamless VPN connectivity.
So let’s go on evaluating each protocol and rank them according to the last-place-first rule.
Position # 4: PPTP – The first to lose the battle is the PPTP. Being
the oldest tunneling protocol out of the bunch, PPTP is widely known to
have considerable security loopholes that can be exploited by skilled
and experienced hackers. Although PPTP is still extensively used, it is
the least secure protocol of the bunch here and that is why it deserves
the last spot on this list.
Position # 3: L2TP IPSEC – The next
to go is the Layer 2 Tunneling Protocol. The L2TP is a successor to the
PPTP with the added support of Internet Protocol Security (IPSec) by
Cisco Systems. Moreover, the L2TP protocol utilizes the L2F or Layer 2
Forwarding capability developed by Cisco Systems. While all this
technology ensures a secure method of data tunneling, it does pose
problems while passing through firewalls, NAT devices, and proxy
servers. Moreover, L2TP requires a pre-shared key for authentication and
this key cannot be absolutely secure.
Position # 2: SSTP – The
successor to the L2TP is the Secure Socket Tunneling Protocol. The SSTP
addresses the problems of the L2TP by utilizing the Hyper Text Transfer
Protocol over a Secure Socket Layer. The use of HTTP on top of SSL
results in a hybrid protocol that is commonly known as HTTPS. HTTPS
technology integrates easily with firewall to ensure seamless operation
of SSTP.
Position # 1: IKEv2 – This is the latest data
tunneling protocol compatible with Windows 7. The Internet Key Exchange
Version 2 employs a wide variety of protocols to tunnel user data like:
Internet Protocol Security Tunnel Mode
Internet Protocol Security Key Negotiation
Encapsulating Security Payload
Mobility and Multi-Homing Protocol
Mobility Manager
Apart from offering the most secure data tunneling and the most
seamless VPN connection, the IKEv2 offers a unique benefit called IP
Persistence. IP Persistence works by maintaining a VPN connection for
the short period of time internet services drop or get disconnected and
then get reconnected again. By holding on to the existing IP address, IP
Persistence ensures that the VPN connection does not have to go through
the entire process of establishing a VPN connection again.
Tuesday, August 13, 2013
Monday, August 5, 2013
Thursday, August 1, 2013
Tuesday, July 9, 2013
Wednesday, April 24, 2013
Thursday, April 11, 2013
How the Internet will travel underwater in 2013 ? (New MAP of Submarine Cables)
Did you know the connectivity of the internet..Here are the
way..Submarine cables ( Cables lying undersea from one region to other
region of the World).
"WELCOME TO THE WORLD OF CABLES"
Stay connected..we will update more information !!
For Interactive MAP visit
http://submarine-cable-map-2013.telegeography.com/
"WELCOME TO THE WORLD OF CABLES"
Stay connected..we will update more information !!
For Interactive MAP visit
http://submarine-cable-map-2013.telegeography.com/

Friday, March 1, 2013
Tuesday, February 12, 2013
Friday, January 25, 2013
Saturday, January 12, 2013
Under the hood of recent DDoS Attack on U.S. Banks
Incapsula security study reveals how a simple neglect in managing the administrative password of a small UK site was quickly exploited by Botnet shepherds operating obscurely out of Turkey to hurl large amounts of traffic at American banks.
If you've been following the news, you are probably aware of a wave of DDoS attacks that recently hit several major U.S. banks. Izz ad-Din al-Qassam, a hacker group that claimed responsibility for these attacks, declared them to be a retaliation for an anti-Islam video that mocked the Prophet Muhammad and a part of the on-going “Operation Ababil.”
As the reports of the attack started to roll in, Incapsula security team was able to uncover one of the secret foot-soldiers behind the assault: a compromised general-interest UK-based website that was trying to hurl large chunks of junk traffic at three of the world's largest financial institutions (PNC, HSBC and Fifth Third Bank).
At On the eve of the attack, this website suddenly became a focal point of a rapidly -increasing number of security events, caused by numerous requests with encoded PHP code payload. Incapsula was able to intercept these requests and traced them back to a backdoor shell that was used to hijack the site.
The backdoor was installed before the website on-boarded Incapsula, and yet the cause of security breach was clear. The administrative password was...you guessed it: admin / admin.
After decoding the incoming PHP requests, the security team could clearly identify them as DDoS attack commands, originating from a Turkish web design company website which was used as a remote Botnet C&C. From the looks of it, the Turkish website was also compromised and used as an additional buffer between the real hacker and its U.S. based targets.
Further investigation showed that the UK website was a part of a Botnet for Hire which was working in “shifts” to produce HTTP and UDP flood attacks. As Incapsula team continued to block and monitor incoming DDoS commands, they saw that the list of targets went beyond American banks, also including e-commerce and commercial websites from several other countries.
Incapsula published the full description of the DDoS attack in the company blog, concluding it by saying that this was just another demonstration of how security on the Internet is always determined by the weakest link. Simple neglect in manage the administrative password of a small UK site, can very quickly be exploited by Botnet shepherds operating obscurely out of Turkey to hurl large amounts of traffic at American banks.
Incapsula Security Analyst, Ronen Atias said: “This is a good example of how we are all just a part of a shared ecosystem where website security should be a shared goal and a shared responsibility.”
Source : THN
Wednesday, January 9, 2013
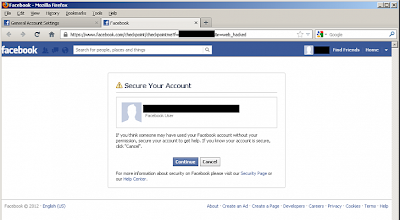
Hacking Facebook Password like chaning your our password
Hacker found a way to hack and change your password like, just he used
to change his own password. Confused ? Recently Facebook fix a very
critical vulnerability on the tip of 'Sow Ching Shiong',
an independent vulnerability researcher. Flaw allows anyone to reset
the password of any Facebook user without knowing his last password.
At Facebook, there is an option for compromised accounts at "https://www.facebook.com/hacked"
, where Facebook ask one to change his password for further protection.
This compromised account recovery page, will redirect you to another
page at "https://www.facebook.com/checkpoint/checkpointme?f=[userid]&r=web_hacked" .
Researcher notice that the URL of the page having a parameter called "f"
which represents your user ID and replacing the user ID with victim's
user ID allow him to get into next page where attacker can reset the
password of victim without knowing his last password.
The Vulnerability was very simple to execute, but now patched by Facebook Security Team.
Subscribe to:
Comments (Atom)